Firewall (computing)
| This article is part of a series on |
| Information security |
|---|
Related security categories |
|
Threats |
|
Defenses |
|
In computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules.[1] A firewall typically establishes a barrier between a trusted internal network and untrusted external network, such as the Internet.[2]
Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls filter traffic between two or more networks and run on network hardware. Host-based firewalls run on host computers and control network traffic in and out of those machines.
Contents
1 History
1.1 First generation: packet filters
1.2 Second generation: stateful filters
1.3 Third generation: application layer
2 Types
2.1 Network layer or packet filters
2.2 Application-layer
2.3 Proxies
2.4 Network address translation
3 See also
4 References
5 External links
History
The term firewall originally referred to a wall intended to confine a fire within a building.[3] Later uses refer to similar structures, such as the metal sheet separating the engine compartment of a vehicle or aircraft from the passenger compartment. The term was applied in the late 1980s to network technology that emerged when the Internet was fairly new in terms of its global use and connectivity.[4] The predecessors to firewalls for network security were the routers used in the late 1980s.[5]
First generation: packet filters
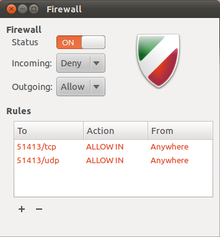
Screenshot of Gufw: The firewall shows its settings for incoming and outgoing traffic.
The first reported type of network firewall is called a packet filter. Packet filters act by inspecting packets transferred between computers. When a packet does not match the packet filter's set of filtering rules, the packet filter either drops (silently discards) the packet, or rejects the packet (discards it and generate an Internet Control Message Protocol notification for the sender) else it is allowed to pass.[6] Packets may be filtered by source and destination network addresses, protocol, source and destination port numbers. The bulk of Internet communication in 20th and early 21st century used either Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) in conjunction with well-known ports, enabling firewalls of that era to distinguish between, and thus control, specific types of traffic (such as web browsing, remote printing, email transmission, file transfer), unless the machines on each side of the packet filter used the same non-standard ports.[7][8]
The first paper published on firewall technology was in 1988, when engineers from Digital Equipment Corporation (DEC) developed filter systems known as packet filter firewalls. At AT&T Bell Labs, Bill Cheswick and Steve Bellovin continued their research in packet filtering and developed a working model for their own company based on their original first generation architecture.[9]
Second generation: stateful filters
From 1989–1990, three colleagues from AT&T Bell Laboratories, Dave Presotto, Janardan Sharma, and Kshitij Nigam, developed the second generation of firewalls, calling them circuit-level gateways.[10]
Second-generation firewalls perform the work of their first-generation predecessors but also maintain knowledge of specific conversations between endpoints by remembering which port number the two IP addresses are using at layer 4 (transport layer) of the OSI model for their conversation, allowing examination of the overall exchange between the nodes.
This type of firewall is potentially vulnerable to denial-of-service attacks that bombard the firewall with fake connections in an attempt to overwhelm the firewall by filling its connection state memory.[11]
Third generation: application layer

Flow of network packets through Netfilter, a Linux kernel module
Marcus Ranum, Wei Xu, and Peter Churchyard released an application firewall known as Firewall Toolkit (FWTK) in October 1993.[12] This became the basis for Gauntlet firewall at Trusted Information Systems.[13][14]
The key benefit of application layer filtering is that it can understand certain applications and protocols (such as File Transfer Protocol (FTP), Domain Name System (DNS), or Hypertext Transfer Protocol (HTTP)). This is useful as it is able to detect if an unwanted application or service is attempting to bypass the firewall using a disallowed protocol on an allowed port, or detect if a protocol is being abused in any harmful way.
As of 2012, the so-called next-generation firewall (NGFW) is nothing more than the "wider" or "deeper" inspection at the application layer. For example, the existing deep packet inspection functionality of modern firewalls can be extended to include:
Intrusion prevention systems (IPS)- User identity management integration (by binding user IDs to IP or MAC addresses for "reputation")
Web application firewall (WAF). WAF attacks may be implemented in the tool "WAF Fingerprinting utilizing timing side channels" (WAFFle)[15]
Types
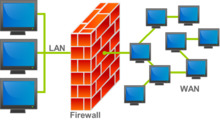
An illustration of where a firewall would be located in a network
Firewalls are generally categorized as network-based or host-based. Network-based firewalls are positioned on the gateway computers of LANs, WANs and intranets. They are either software appliances running on general-purpose hardware, or hardware-based firewall computer appliances. Firewall appliances may also offer other functionality to the internal network they protect, such as acting as a DHCP[16][17] or VPN[18][19][20][21] server for that network.[22][23] Host-based firewalls are positioned on the network node itself and control network traffic in and out of those machines.[24][25] The host-based firewall may be a daemon or service as a part of the operating system or an agent application such as endpoint security or protection. Each has advantages and disadvantages. However, each has a role in layered security.
Firewalls also vary in type depending on where communication originates, where it is intercepted, and the state of communication being traced.[26]
Network layer or packet filters
Network layer firewalls, also called packet filters, operate at a relatively low level of the TCP/IP protocol stack, not allowing packets to pass through the firewall unless they match the established rule set. The firewall administrator may define the rules; or default rules may apply. The term "packet filter" originated in the context of BSD operating systems.
Network layer firewalls generally fall into two sub-categories, stateful and stateless.
Commonly used packet filters on various versions of Unix are ipfw (FreeBSD, Mac OS X (< 10.7)), NPF (NetBSD), PF (Mac OS X (> 10.4), OpenBSD, and some other BSDs), iptables/ipchains (Linux) and IPFilter.[citation needed]
Application-layer
Application-layer firewalls work on the application level of the TCP/IP stack (i.e., all browser traffic, or all telnet or FTP traffic), and may intercept all packets traveling to or from an application.
Application firewalls function by determining whether a process should accept any given connection. Application firewalls accomplish their function by hooking into socket calls to filter the connections between the application layer and the lower layers of the OSI model. Application firewalls that hook into socket calls are also referred to as socket filters. Application firewalls work much like a packet filter but application filters apply filtering rules (allow/block) on a per process basis instead of filtering connections on a per port basis. Generally, prompts are used to define rules for processes that have not yet received a connection. It is rare to find application firewalls not combined or used in conjunction with a packet filter.[27]
Also, application firewalls further filter connections by examining the process ID of data packets against a rule set for the local process involved in the data transmission. The extent of the filtering that occurs is defined by the provided rule set. Given the variety of software that exists, application firewalls only have more complex rule sets for the standard services, such as sharing services. These per-process rule sets have limited efficacy in filtering every possible association that may occur with other processes. Also, these per-process rule sets cannot defend against modification of the process via exploitation, such as memory corruption exploits. Because of these limitations, application firewalls are beginning to be supplanted by a new generation of application firewalls that rely on mandatory access control (MAC), also referred to as sandboxing, to protect vulnerable services.[28]
Proxies
A proxy server (running either on dedicated hardware or as software on a general-purpose machine) may act as a firewall by responding to input packets (connection requests, for example) in the manner of an application, while blocking other packets. A proxy server is a gateway from one network to another for a specific network application, in the sense that it functions as a proxy on behalf of the network user.[2]
Proxies make tampering with an internal system from the external network more difficult, so that misuse of one internal system would not necessarily cause a security breach exploitable from outside the firewall (as long as the application proxy remains intact and properly configured). Conversely, intruders may hijack a publicly reachable system and use it as a proxy for their own purposes; the proxy then masquerades as that system to other internal machines. While use of internal address spaces enhances security, crackers may still employ methods such as IP spoofing to attempt to pass packets to a target network.
Network address translation
Firewalls often have network address translation (NAT) functionality, and the hosts protected behind a firewall commonly have addresses in the "private address range", as defined in RFC 1918. Firewalls often have such functionality to hide the true address of computer which is connected to the network. Originally, the NAT function was developed to address the limited number of IPv4 routable addresses that could be used or assigned to companies or individuals as well as reduce both the amount and therefore cost of obtaining enough public addresses for every computer in an organization. Although NAT on its own is not considered a security feature, hiding the addresses of protected devices has become an often used defense against network reconnaissance.[29]
See also
- Access control list
- Air gap (networking)
- Bastion host
- Comparison of firewalls
- Computer security
- De-perimeterisation
- Distributed firewall
- Egress filtering
- End-to-end principle
- Firewall pinhole
- Firewalls and Internet Security
- Golden Shield Project
- Guard (information security)
- Identity-based security
- IP fragmentation attacks
- List of Unix-like router or firewall distributions
- Mangled packet
- Mobile security § Security software
- Next-Generation Firewall
- Personal firewall
- Screened subnet
- Unidirectional network
- Virtual firewall
- Vulnerability scanner
- Windows Firewall
References
^ Boudriga, Noureddine (2010). Security of mobile communications. Boca Raton: CRC Press. pp. 32–33. ISBN 0849379423..mw-parser-output cite.citationfont-style:inherit.mw-parser-output .citation qquotes:"""""""'""'".mw-parser-output .citation .cs1-lock-free abackground:url("//upload.wikimedia.org/wikipedia/commons/thumb/6/65/Lock-green.svg/9px-Lock-green.svg.png")no-repeat;background-position:right .1em center.mw-parser-output .citation .cs1-lock-limited a,.mw-parser-output .citation .cs1-lock-registration abackground:url("//upload.wikimedia.org/wikipedia/commons/thumb/d/d6/Lock-gray-alt-2.svg/9px-Lock-gray-alt-2.svg.png")no-repeat;background-position:right .1em center.mw-parser-output .citation .cs1-lock-subscription abackground:url("//upload.wikimedia.org/wikipedia/commons/thumb/a/aa/Lock-red-alt-2.svg/9px-Lock-red-alt-2.svg.png")no-repeat;background-position:right .1em center.mw-parser-output .cs1-subscription,.mw-parser-output .cs1-registrationcolor:#555.mw-parser-output .cs1-subscription span,.mw-parser-output .cs1-registration spanborder-bottom:1px dotted;cursor:help.mw-parser-output .cs1-ws-icon abackground:url("//upload.wikimedia.org/wikipedia/commons/thumb/4/4c/Wikisource-logo.svg/12px-Wikisource-logo.svg.png")no-repeat;background-position:right .1em center.mw-parser-output code.cs1-codecolor:inherit;background:inherit;border:inherit;padding:inherit.mw-parser-output .cs1-hidden-errordisplay:none;font-size:100%.mw-parser-output .cs1-visible-errorfont-size:100%.mw-parser-output .cs1-maintdisplay:none;color:#33aa33;margin-left:0.3em.mw-parser-output .cs1-subscription,.mw-parser-output .cs1-registration,.mw-parser-output .cs1-formatfont-size:95%.mw-parser-output .cs1-kern-left,.mw-parser-output .cs1-kern-wl-leftpadding-left:0.2em.mw-parser-output .cs1-kern-right,.mw-parser-output .cs1-kern-wl-rightpadding-right:0.2em
^ ab Oppliger, Rolf (May 1997). "Internet Security: FIREWALLS and BEYOND". Communications of the ACM. 40 (5): 94. doi:10.1145/253769.253802.
^ Canavan, John E. (2001). Fundamentals of Network Security (1st ed.). Boston, MA: Artech House. p. 212. ISBN 9781580531764.
^ Liska, Allan (Dec 10, 2014). Building an Intelligence-Led Security Program. Syngress. p. 3. ISBN 0128023708.
^ Ingham, Kenneth; Forrest, Stephanie (2002). "A History and Survey of Network Firewalls" (PDF). Retrieved 2011-11-25.
^ Peltier, Justin; Peltier, Thomas R. (2007). Complete Guide to CISM Certification. Hoboken: CRC Press. p. 210. ISBN 9781420013252.
^ "TCP vs. UDP : The Difference Between them". www.skullbox.net. Retrieved 2018-04-09.
^ William R. Cheswick, Steven M. Bellovin, Aviel D. Rubin (2003). "Google Books Link". Firewalls and Internet Security: repelling the wily hacker
^ Ingham, Kenneth; Forrest, Stephanie (2002). "A History and Survey of Network Firewalls" (PDF). p. 4. Retrieved 2011-11-25.
^ M. Afshar Alam; Tamanna Siddiqui; K. R. Seeja (2013). Recent Developments in Computing and Its Applications. I. K. International Pvt Ltd. p. 513. ISBN 978-93-80026-78-7.
^ Chang, Rocky (October 2002). "Defending Against Flooding-Based Distributed Denial-of-Service Attacks: A Tutorial". IEEE Communications Magazine. 40 (10): 42–43. doi:10.1109/mcom.2002.1039856.
^ "Firewall toolkit V1.0 release". Retrieved 2018-12-28.
^ John Pescatore (October 2, 2008). "This Week in Network Security History: The Firewall Toolkit". Retrieved 2018-12-28.
^ Marcus J. Ranum; Frederick Avolio. "FWTK history".
^ "WAFFle: Fingerprinting Filter Rules of Web Application Firewalls". 2012.
^ "Firewall as a DHCP Server and Client". Palo Alto Networks. Retrieved 2016-02-08.
^ "DHCP". www.shorewall.net. Retrieved 2016-02-08.
^ "What is a VPN Firewall? – Definition from Techopedia". Techopedia.com. Retrieved 2016-02-08.
^ "VPNs and Firewalls". technet.microsoft.com. Retrieved 2016-02-08.
^ "VPN and Firewalls (Windows Server)". Resources and Tools for IT Professionals | TechNet.
^ "Configuring VPN connections with firewalls".
^ Andrés, Steven; Kenyon, Brian; Cohen, Jody Marc; Johnson, Nate; Dolly, Justin (2004). Birkholz, Erik Pack, ed. Security Sage's Guide to Hardening the Network Infrastructure. Rockland, MA: Syngress. pp. 94–95. ISBN 9780080480831.
^ Naveen, Sharanya. "Firewall". Retrieved 7 June 2016.
^ Vacca, John R. (2009). Computer and information security handbook. Amsterdam: Elsevier. p. 355. ISBN 9780080921945.
^ "What is Firewall?". Retrieved 2015-02-12.
^ "Firewalls". MemeBridge. Retrieved 13 June 2014.
^ "Software Firewalls: Made of Straw? Part 1 of 2". Symantec Connect Community. 2010-06-29. Retrieved 2014-03-28.
^ "Auto Sandboxing". Comodo Inc. Retrieved 2014-08-28.
^ "Advanced Security: Firewall". Microsoft. Retrieved 2014-08-28.
External links
| The Wikibook Guide to Unix has a page on the topic of: OpenBSD PF firewall |
| Wikimedia Commons has media related to Firewall. |
Internet Firewalls: Frequently Asked Questions, compiled by Matt Curtin, Marcus Ranum and Paul Robertson.
Firewalls Aren’t Just About Security – Cyberoam Whitepaper focusing on Cloud Applications Forcing Firewalls to Enable Productivity.
Evolution of the Firewall Industry – Discusses different architectures and their differences, how packets are processed, and provides a timeline of the evolution.
A History and Survey of Network Firewalls – provides an overview of firewalls at the various ISO levels, with references to the original papers where first firewall work was reported.
Software Firewalls: Made of Straw? Part 1 and Software Firewalls: Made of Straw? Part 2 – a technical view on software firewall design and potential weaknesses
Why the Future of Firewall Security will be Context-Based – GajShield Whitepaper providing an insight on how Context based security will empower the future of firewall security.
